
No secret, the Internet space is huge nowadays. Unfortunately, alongside the unprecedented information opportunities, we face numerous dangers and even cyber-attacks. That is why being on the alert is a must for every Internet user, no matter how one secures their online activity – it can vary a lot and arises to an individual choice. Whatever technique or tool you apply, make sure your ‘security system’ uses data encryption methods and does not allow the third parties to analyze the traffic or monitor your online activity (this is what Internet providers often do).
We decided to suggest you an effective way to ensure double-layer security, based on using TOR together with a VPN. The topic is highly controversial, in fact: the debate starts from whether to use TOR with a VPN at all and finishes with questions about the ways to combine these two technologies.
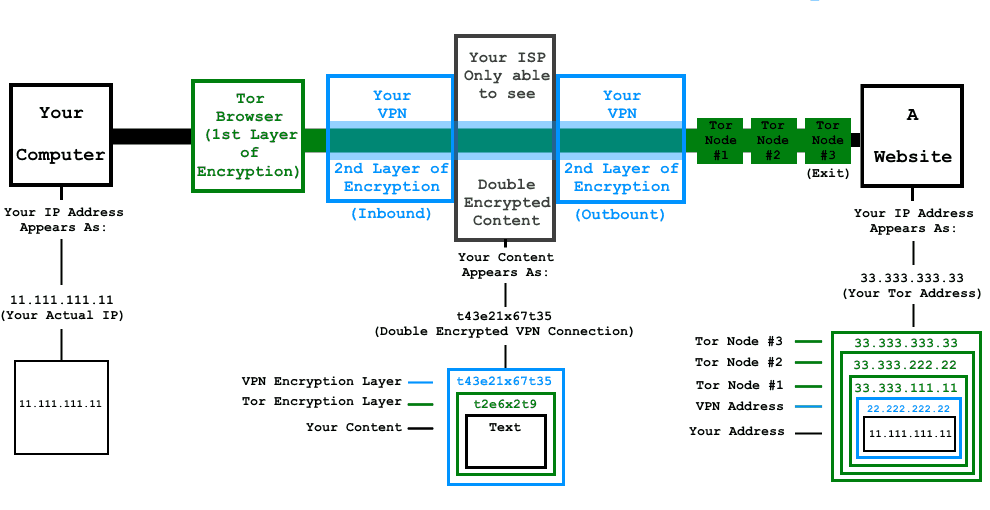
Why consider combinations TOR+VPN?
While a VPN guarantees higher speeds compared to TOR, it provides no anonymity. Great if you have chosen a VPN that uses at least 128-bit encryption. However, it is way better to ensure 256-bit encryption with TOR, since this will considerably raise your chances to prevent snooping.
In addition, it is extremely hard to find a VPN provider that keeps no logs of your activity. Even if they claim to not retain logs, there is no proof they don’t. Of course, a VPN provider would rather avoid being prosecuted rather than lose one subscriber, as long as performing no data logging contradicts the state laws. But if you combine TOR with the VPN, the only thing visible from the log will be an anonymous TOR user. Plus the IP address given by TOR will serve an amazing fall back in case the VPN connection drops.
Another benefit is that your TOR activity can be hidden from the websites blocking TOR users: the VPN connection will appear as the exit node, which most likely helps bypass the filters. Moreover, VPN will keep your data encrypted in a force majeure when passing through a compromised TOR exit node.
The only vital sacrifice you should be aware of when combining TOR and a VPN is the connection speed.
How to combine
TOR and a VPN can be combined within two basic configurations. Both have their pros and cons to be taken into account with reference to certain security needs:
| TOR through VPN | VPN through TOR | |
| VPN provider sees your real IP-address | yes | no |
| Protection from malicious TOR exit nodes | no | yes |
| Possible blockage on TOR exit nodes | yes | no |
| The ISP sees that you use TOR | no | yes |
- TOR through VPN
The configuration implies connecting to the VPN server, then accessing the TOR network and after that proceeding to the Internet (including TOR hidden services – .onion websites!). The setup process is relatively easy if you use a VPN service based on OpenVPN protocol (like NordVPN or TorVPN):- connect to the VPN
- make sure your IP-address has changed
- open TOR.
For proper security, it is recommended to use the TOR browser, equipped with more safety features if compared to other browsers.
- VPN through TOR
This configuration is widely considered more secure given the true anonymity it provides, even despite higher vulnerability to the global end-to-end timing attack. However, the setup process is more complicated due to OpenVPN reconfiguration of the network routes, which does not allow TOR to run on the same host.
To overcome the reconfiguration issue, it is possible to use the VPN services, where the VPN client is appropriately configured automatically – AirVPN or BolehVPN.If you use another VPN service, the setup can be performed via a virtual machine, added by installation and running of such tools as TOR Expert and Tortilla:- install and start running a virtual machine (e.g. Virtual Box)
- run TOR Expert and Tortilla on the host OS
- set the VM to route all the traffic via Tortilla (bridge adapter, for now only supported by Windows)
- connect to a VPN
- make sure your IP-address has changed.
To add even more security layers, you can install and run TOR browser bundle on the VM, which will result in TOR-VPN-TOR. Plus, you can build VPN-TOR-VPN-TOR if you start with using a VPN on the host OS. Note that extra layers lead to speed leaks.
Remember that any combination TOR+VPN will definitely cover the weaknesses of each stand-alone technology.